Anywhere365 - Troubleshooting your SharePoint application
If you work a lot with Anywhere365 you are familiar with the core setup and how configurations are being handled (by caching), so if you clear the caching while rebooting the UCC’s and all kind of strange error’s show up (i.e. new agents not visible, IVR changes not showing) there are a couple of items that can be your nightmare:
- App Secret
- Permissions on Anywhere365 SharePoint site
- SharePoint global Settings
I’d like to take you through how I would approach this.
App Secret
In case your App Secret is exprired you can simply renew the secret based on your App Id. You can also check if Secrets have been expired by the following cmdlets.
Connect-MsolService
$clientID = "4f327b5c-d62d-40ef-974b-38bcd3f8527c" # Update to application client ID
Get-MsolServicePrincipal -AppPrincipalId $clientID
$keys = Get-MsolServicePrincipalCredential -AppPrincipalId $clientID -ReturnKeyValues $true
$keys |ft Type, KeyId, StartDate,EndDate
In the following example you are able to renew the App Secret for 3 years. (replace the clientId with your own)
Connect-MsolService
$clientId = '4f327b5c-d62d-40ef-974b-38bcd3f8527c'
$bytes = New-Object Byte[] 32
$rand = [System.Security.Cryptography.RandomNumberGenerator]::Create()
$rand.GetBytes($bytes)
$rand.Dispose()
$newClientSecret = [System.Convert]::ToBase64String($bytes)
$dtStart = [System.DateTime]::Now
$dtEnd = $dtStart.AddYears(3)
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Symmetric -Usage Sign -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Symmetric -Usage Verify -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
New-MsolServicePrincipalCredential -AppPrincipalId $clientId -Type Password -Usage Verify -Value $newClientSecret -StartDate $dtStart -EndDate $dtEnd
Write-Host "Your new Client Secret: $newClientSecret "
You will need to edit the config.xml and replace the App Secret (for all UCC’s) with the newly generated secret. If this will not fix your issue, proceed to the next chapter.
SharePoint Site Permissions
From the deployments steps where initialy you have created the App Id, you will need to grant permissions to the Anywhere Config Template (verify this).
Go to the following URL:
<Site Collection URL>/_layouts/15/AppInv.aspx
Lookup you App Id and fill the Permissions Request URL with the following code:
<AppPermissionRequests AllowAppOnlyPolicy="true">
<AppPermissionRequest Scope="http://sharepoint/content/sitecollection" Right="FullControl"/>
</AppPermissionRequests>
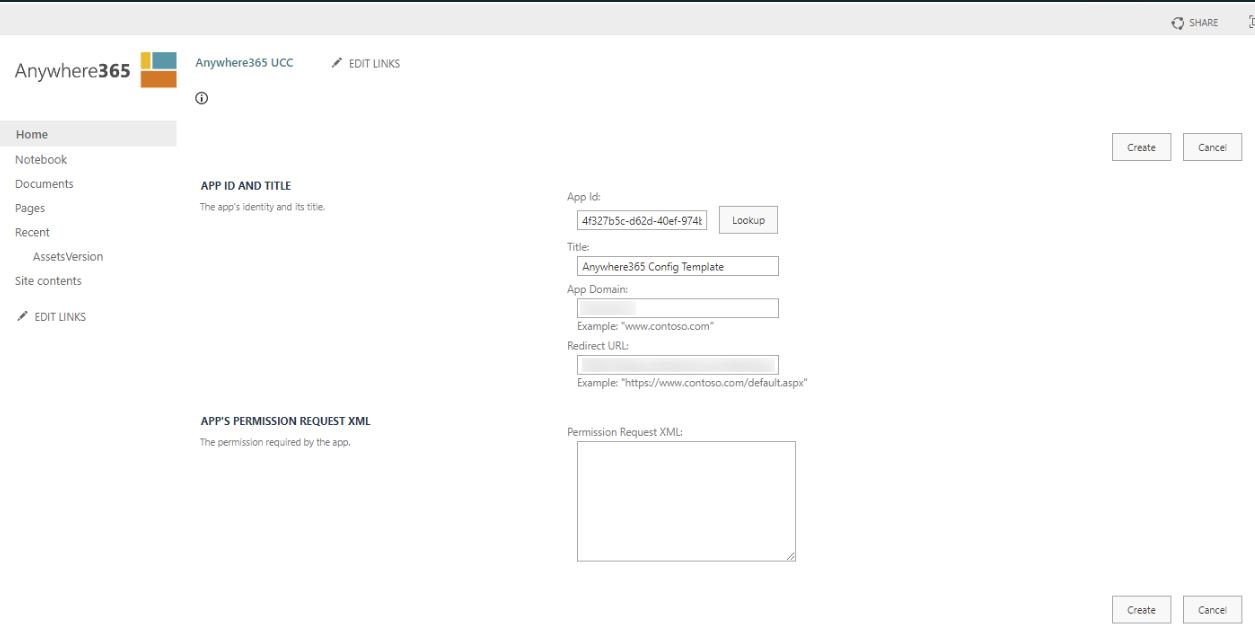
Hit the create button and select Trust It! on the next step. Is this still not resolving your issue, we need to look in to the global settings.
SharePoint global settings
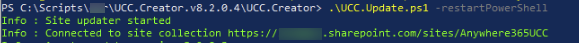
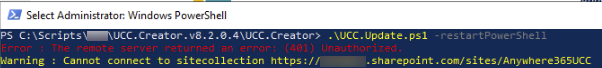
If you are gettings errors connection to the SharePoint Collection with the App Id and App Secret (error 401) we are going to check the SharePoint global settings.
Install SharePoint Online PowerShell module.
Install-Module -Name Microsoft.Online.SharePoint.PowerShell
Connect to SharePoint online.
Connect-SPOService
When prompted connect to the Url of your SharePoint Admin site (Like https://-admin.sharepoint.com), and login with your administrator credentials.
Lookup the following cmdlet.
Get-SPOTenant | FL DisableCustomAppAuthentication
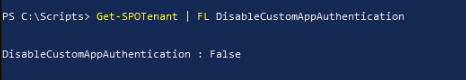
If the value returns with TRUE you have found the issue. In order to let the Custom App from Anywhere365 connect you will need to enable Custom App Authentication
You can enable Custom App Authentication by the following command:
Set-SPOtenant -DisableCustomAppAuthentication $false
Wait for a couple of minutes and try again.