Let’s Encrypt and Skype for Business
For my home lab I’m using the free certificates from Let’s Encrypt (Let’s Encrypt is a free, automated, and open Certificate Authority).
The certificates from them have 1 big limitation, they are only valid for 3 months but you can renew them “almost” automatically.
As explained In my blog last week about “Skype for Business environment running with just one public IP” I’m running my Reverse Proxy with IIS ARR (Application Request Routing). I’ll try to explain how to request and assign the free certificates for your homelab.
Configuration IIS ARR
Follow the instruction from my other blog “How to configure IIS ARR for Skype for Business”
Firewall Settings
Make sure you open the following ports on your firewall, for the check only 80/443 are required.
Source
Destination
Port
Protocol
Note
Any
192.168.178.34
443
TCP
To Reverse Proxy
Any
192.168.178.34
80
TCP
To Reverse Proxy
DNS Settings
In the next chapter you’re going to request the certificates. The mechanism works as follows: The executable is going to resolve the subdomain, so all the subdomains you want to create needs to exist on your public DNS provider.
For every resolve Let’s Encrypt is creating a cache file the .well-known folder in your webroot directory (C:\inetpub\wwwroot.well-known) This is to validate your permission for the certificate.
For my lab setup I’m using the following records:
Name
Type
Value
Access.skypedev.nl
A
84.27.37.88
Dialin.skypedev.nl
A
84.27.37.88
Lyncdiscover.skypedev.nl
A
84.27.37.88
Meet.skypedev.nl
A
84.27.37.88
Sip.skypedev.nl
A
84.27.37.88
Skypeweb.skypedev.nl
A
84.27.37.88
Request Certificate
Download the Let’s encrypt tool from here: Link Create a directory C:\Central_SSL Start your command prompt and go to the letsencrypt directory:
.\letsencrypt.exe --san --centralsslstore C:\Central_SSL\ --accepttos
First time, enter your email address: name@domain.com Choose for option:
M
Enter a hostname, I’m using Access.skypedev.nl so this will be my common name. Now paste the list of subdomains you will need:
Access.skypedev.nl,dialin.skypedev.nl,lyncdiscover.skypedev.nl,meet.skypedev.nl,sip.skypedev.nl,skypeweb.skypedev.nl
Enter a site path:
C:\inetpub\wwwroot
Now you will be asked if you want to create a Scheduled Task, and if a special user must run this script.

Now look in the c:\Central_SSL folder and you will see all certificates. All certificates are the same only with a different name. Copy the access.skypedev.nl to the Edge Server and import certificate, below how to assign to IIS.
Assign Certificate to IIS
You only need to assign the certificate to your IIS
Click your IIS Server in IIS Manager
Click “Server Certificates”
On the right menu, choose “Import”
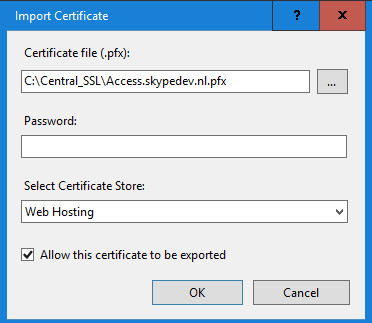
Go to the C:\Central_SSL directory and select the “Acces.Skypedev.nl”
There is no password on the file, Select “Web Hosting” from the certificate store and click “OK”
Now right click your “Default Web Site” and select “Bindings”
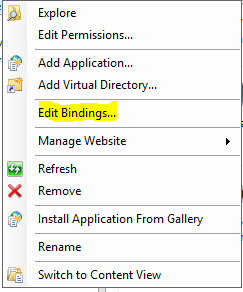
Click the 443 rule and click “Edit”
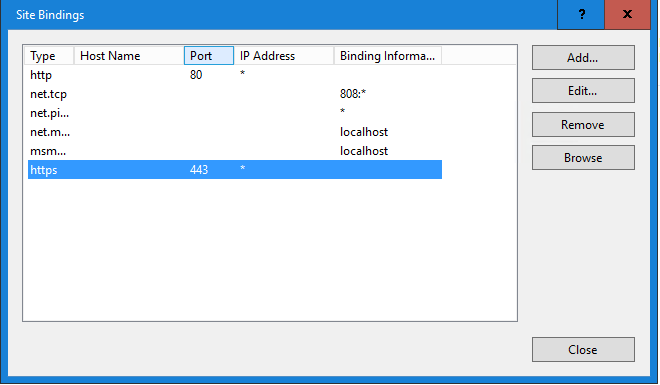
Selet the certificate from the list and click “Ok”
Now only reset your IIS and you’re ready to roll

Assign Certicate to Skype for Business Edge Server
Login to your Edge Server. Copy the PFX file to your desktop.
Now open your Skype for Business Deployment Wizard.
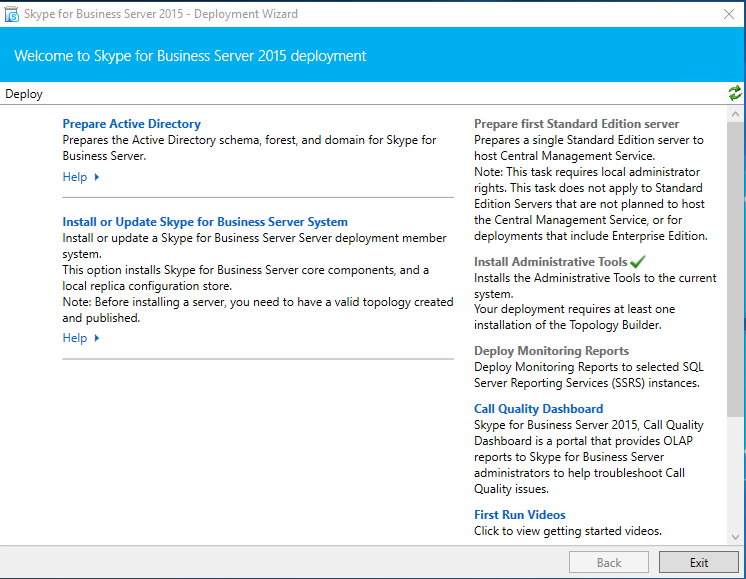
Go to “Install and Update Skype for Business Server System”
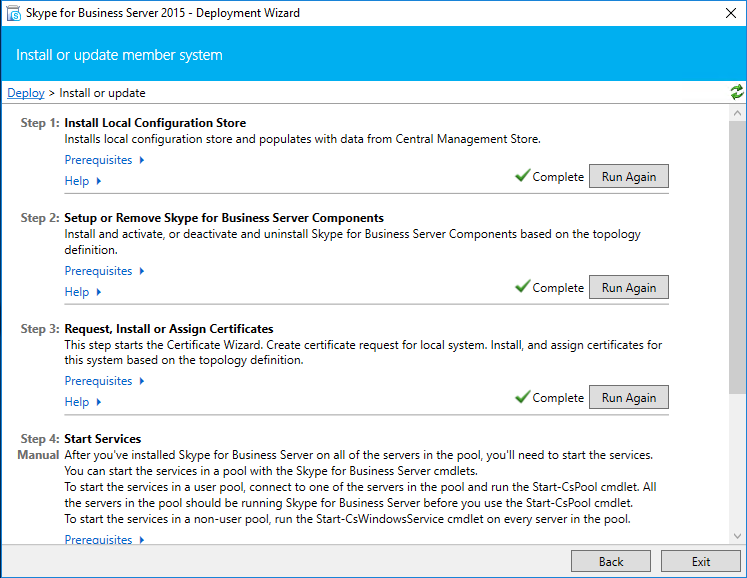
Click “Run Again” at Step 3 request, Install or Assign Certificates.
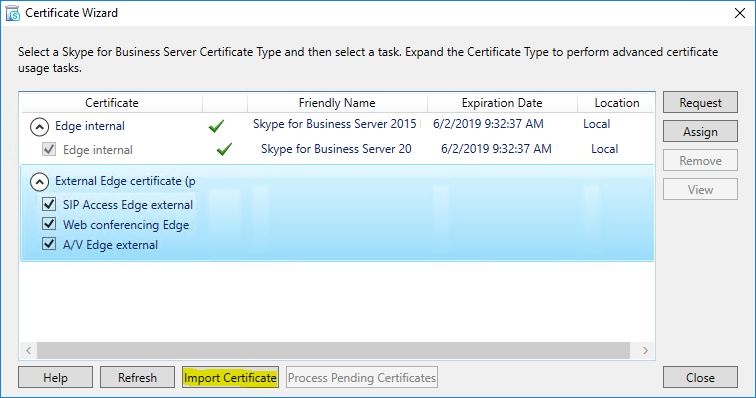
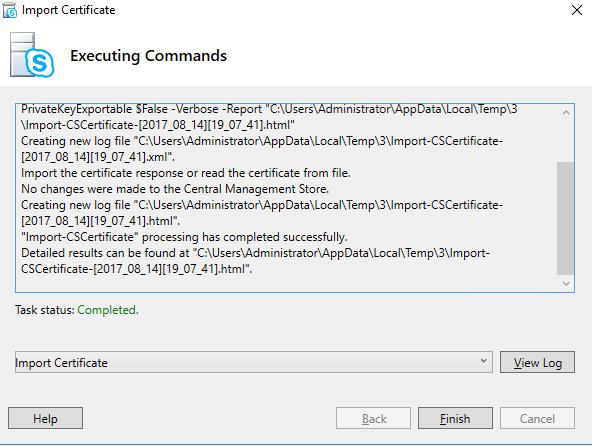
Click “Import Certificate”
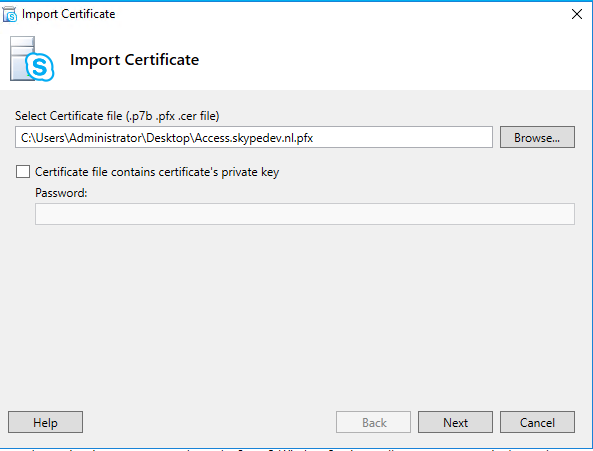
Go to your path where you copied your certificate and click “Next”, “Next” “Finish”.
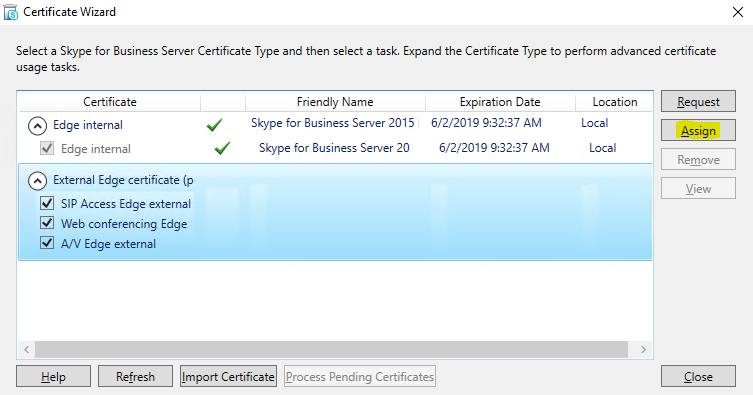
Now select your external Edge Certificate and click “Assign”
Click “Next” on the first screen, Now select your (external) certificate.
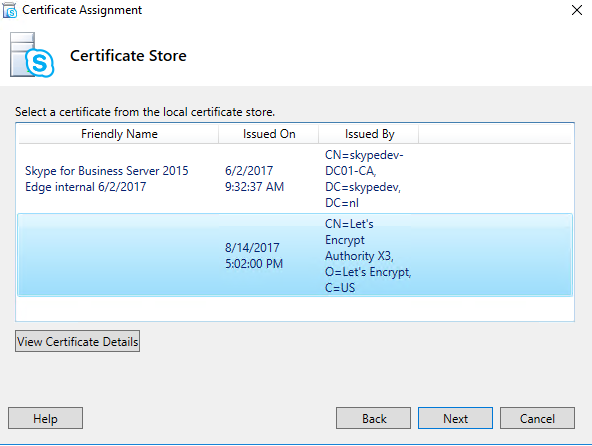
After selecting click “Next”, “Next”, Finish.
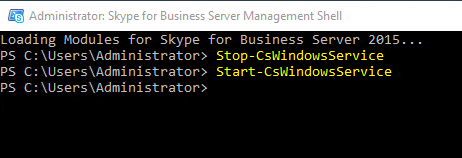
Open your Skype for Business Managemnt Shell and stop/start your Skype services.
Happy Skyping! :-)
If you have any suggestions or questions, please feel free to ask in the comments.
/
